The most frequent cyber security alarms in 2023 and the importance of continuous monitoring
The most frequent cyber security alarms in 2023 and the importance of continuous monitoring
06.07.2024.

The most frequent cyber security alarms in 2023 and the importance of continuous monitoring
Understanding the business environment, identifying potential risks, and quick response to any security event are key in setting up a defensive strategy. Throughout 2023, we implemented proactive and reactive measures through our Security Operations Center (SOC) and Early Alerting services.
The human role through Threat Hunting operations, guided by expertise and creativity, has proven absolutely irreplaceable in detecting advanced threats in users that traditional protection systems failed to register.
TOP 10 most frequently addressed cyber security alarms in 2023
Within the Security Operations Center (SOC), we are dedicated to monitoring and analyzing cyber threats to ensure the highest level of security for our users. In the operations conducted, we focused on monitoring security alarms according to MITRE ATT&CK tactics, which enable us to identify the most common threats and security events.
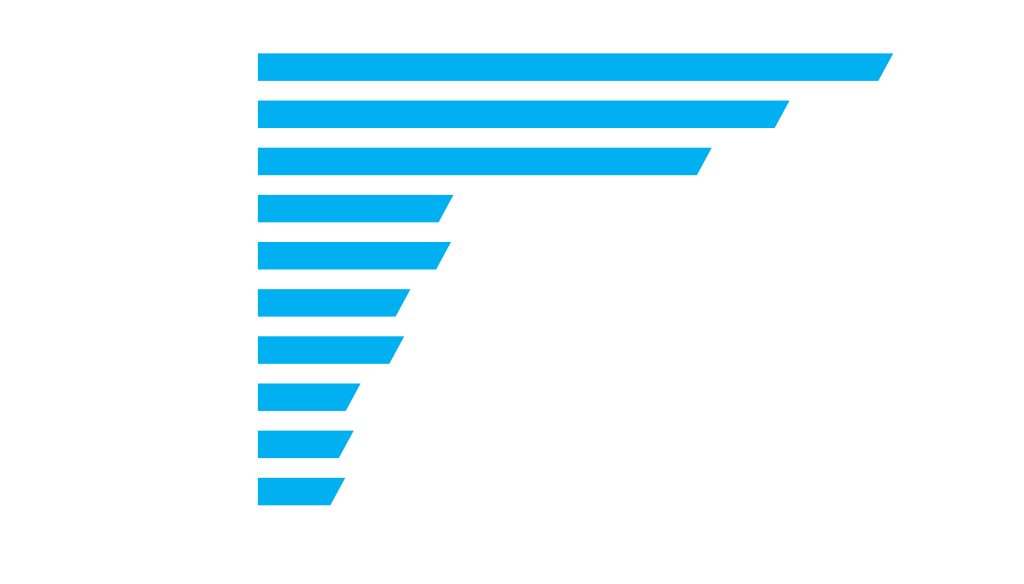
Figure 1. TOP 10 most frequently addressed alarms according to MITRE ATT&CK tactics in 2023 [Source: Diverto SOC]
In addition to a general increase in the number of threats, this natural growth is the result of a systematic expansion of our SOC’s capacity, particularly in the number of SOC users, the volume of new devices, and supported technologies that we actively monitor, as well as the improvement of security operations within the provision of the Security Operations Center service.
Trend of the TOP 5 most frequently addressed alarms
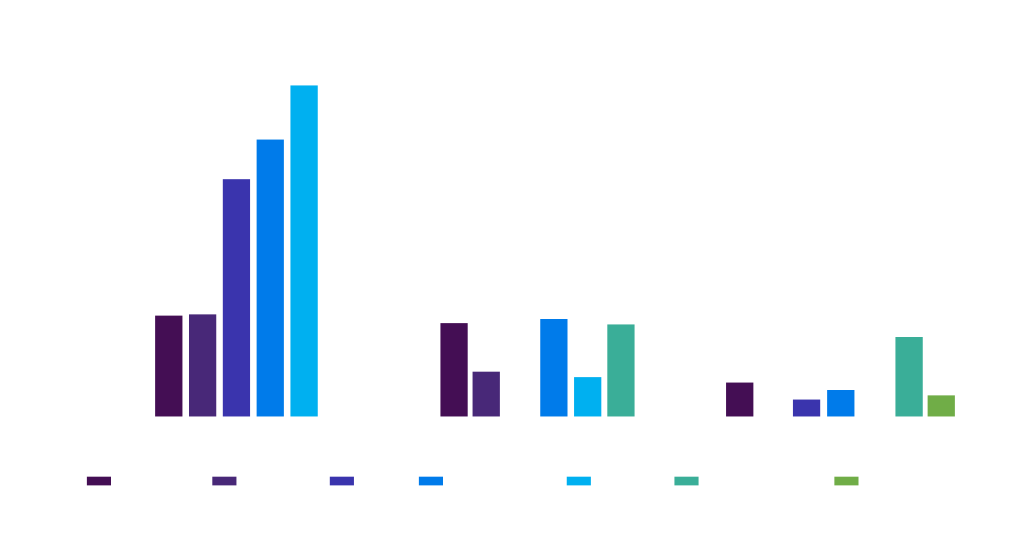
Figure 2. TOP 5 most frequently addressed alarms according to MITRE ATT&CK tactics in 2023, 2022, and 2021 [Source: Diverto SOC]
The foundation for organizations to take preventive action in facing the challenges of increasingly sophisticated cyber threats is timely response to identified threats and vulnerabilities. With a wide range of different services utilized by users, monitoring and managing vulnerabilities has become increasingly demanding.
Every year, users face the challenge of timely responding, managing threats, and vulnerabilities. This complexity leads to an increased risk of exploiting vulnerabilities, with potentially serious consequences for information security and system integrity.
Timely installation of security patches
In the past year, Diverto’s users have made significant progress in managing and protecting information assets, and as part of the Early Warning System service, they received security notifications about threats and vulnerabilities in their system. The solution for 93% of the vulnerabilities published during 2023 was in the form of timely installation of security patches.
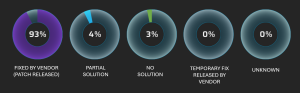
Figure 3. Total number of security notifications, grouped by “Solution Status” [Source: Diverto]
The imperative and main recommendation remains to strengthen the security of external access points in order to reduce the possibility of exploiting system vulnerabilities and ensure data integrity.
Security notifications with the most significant impact
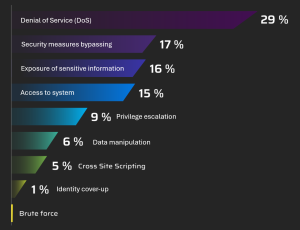
Figure 4. Total number of security notifications, grouped by “Impact” [Source: Diverto]
KAs the most significant key security notifications within our SOC during the last year, we would highlight:
- “Denial of Service – DoS,”
- “Bypassing Security Measures,”
- “Exposure of Sensitive Information,”
- “System Access,”
considering that they represent a significant challenge to system security and account for 77% of all identified vulnerabilities during 2023.
Feel free to download the complete annual report with numerous interesting data and insights by clicking on the link: “State of information and cybersecurity in 2023″.
Recommendations for Strengthening the System’s Defensive Strategy
We recommend the regular identification and updating of a complete information assets inventory. This includes all systems, network devices, databases, and other security technologies and components that make up your infrastructure. Accurate definition of information assets is crucial for properly directing security efforts.
We emphasize the importance of timely system updates through the installation of security patches. Active monitoring of available patches and their rapid implementation reduces the risk of exploiting known vulnerabilities.
Additionally, we recommend directing resources and processes towards timely analysis of security events to enable quick detection of unusual activities. The use of log analysis tools and the implementation of an early alerting system contributes to enhancing the organization’s ability to recognize and respond to potential threats.
Identified vulnerabilities should be a key focus for further strengthening defensive mechanisms. It is recommended to focus on implementing additional security controls, conducting additional security tests, and educating staff about new threats and vulnerabilities.
„Faced with the challenges of increasingly complex cyber threats, continually updating defensive strategy perspectives, with a special emphasis on the key role of the SOC, ensures an effective response to the dynamics of the cyber environment. By strengthening security capacities and proactively monitoring new threats, we are laying the foundations for the stability and reliability of the organization’s information resources.”
DAVOR SLAVICA
defense team lead
What do the law and regulations say?
NIS2, i.e., the Cybersecurity Act (CSA) and DORA, prescribe to obligees the requirement to establish measures for managing cybersecurity risks, which among others must include:
- handling incidents, including their monitoring, recording, and reporting; and
- regular updating of the asset inventory.
The Security Operations Center plays a key role in the incident management process. The SOC ensures continuous monitoring of activities on the network and information systems of IT and OT networks and timely detection of potential security incidents. Within the SOC, security events are collected and recorded according to a defined classification.
Also, both within CSA and DORA, the precise definition of information assets is recognized as important for properly directing security efforts. With an up-to-date inventory of information and ICT assets and the Early Alerting service, you can timely recognize and respond to identified vulnerabilities.
Check if you are compliant with the NIS2 Directive
To more easily determine the level of compliance of your organization with the NIS2 Directive, download the self-assessment tool. Discover in which areas you are compliant and where there is room for improvement.
CONDUCT SELF-ASSESSMENT