Key challenges and (un)preparedness of the organization for NIS2 and DORA
Key challenges and (un)preparedness of organizations for NIS2 and DORA
06.07.2024.

Key challenges and (un)preparedness of organizations for NIS2 and DORA-u
The new EU regulatory frameworks brought by NIS2 and DORA are certainly expected to increase the level of security maturity for numerous organizations and their operations. However, even though it is a positive step forward, according to the results of the research we conducted for our large annual report, “State of information and cybersecurity in 2023“, NIS2 and DORA are sources of many questions and challenges.
Management awareness on NIS2 and DORA requirements Razina svijesti poslovodstva o zahtjevima NIS2 i DORA-e
Our findings indicate that the managements of organizations are not equally informed about the NIS2 Directive and the new obligations and responsibilities that arise from it. This primarily refers to entities that will be classified as important and who will become subjects to the Cybersecurity Act.
Some of the entities from new sectors within the scope (e.g., telecommunications, postal services, manufacturing) have so far been regulated by laws specific to their industry and area of operation, while information and cybersecurity protection has not typically been the focus.
On the other hand, as expected, the financial industry, which is accustomed to high demands of information and cybersecurity, leads in activities undertaken to ensure the required level of compliance with DORA.
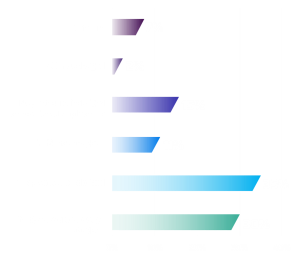
Figure 1. Do you know what the adoption of NIS2 / CRA / DORA regulations means for your organization?, [Source: Diverto]
35% of organizations are aware that they will become new subjects of one of the mentioned regulations and know what that means for them, while 22% of organizations are not sure what the new regulations will mean for them nor whether any of the regulations apply to them.
Prepare a budget for compliance
To implement the requirements arising from the new regulations, it is necessary to timely allocate an appropriate budget.
Based on the data we have collected, organizations that are aware and certain that they will be subjects to the NIS2/CRA/DORA regulations allocate a higher percentage of the IT budget compared to all surveyed organizations in 2022 and 2023.
This is most evident from the fact that 23% of the obligated entities allocate more than 5% and less than 10% of the IT budget for information/cybersecurity, compared to 18% of all surveyed organizations in 2023, and 21% of organizations in 2022.
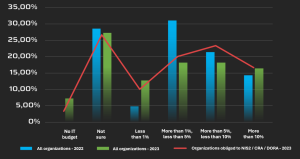
Figure 2. Budget allocation for information/cybersecurity among organizations that are aware and certain they will be subject to NIS2/DORA/CRA regulations compared to all surveyed organizations this year and last year. [Source: Diverto]
Organizations obligated to regulations that have not allocated funds for compliance most commonly:
→ are not aware of the regulatory requirements related to information and cybersecurity nor whether they will apply to them,
→ are aware of the regulations, but believe there is sufficient time to comply,
→ are aware of the regulations, but believe that the regulations, especially NIS2, will not be implemented in the way they are defined, which is why they do not fear sanctions.
Shortage of Cybersecurity Experts
With new regulatory requirements and the fact that there is generally a significant shortage of human resources in the field of information and cybersecurity, it is expected that this will pose an even greater challenge in the coming years than it has been so far. The significant increase in demand for resources will be influenced by organizations that have not managed information and cybersecurity adequately or at all until now.
Given the limited supply of resources in the market and the inability to build capacity for managing information and cybersecurity “internally,” organizations are increasingly recognizing the practicality and added value of outsourced services such as Cyber Threat Intelligence, vCISO, and Security Operations Centers.
- 70% of surveyed organizations that are aware and certain they will be subject to NIS2/DORA/CRA regulations have allocated budgets for compliance purposes.
- 40% of the same have concluded that they will not be able to carry out compliance activities independently.
- 50% of organizations that are not sure what the new regulations will mean for them or whether any of the regulations apply to them do not have IT budgets or are not sure what percentage of the IT budget they have available for information and cybersecurity needs.
- 80% of organizations that are aware and certain they will be subject to NIS2/DORA/CRA regulations believe that investments in information and cybersecurity enable safe business operations and resilience to cyber attacks.
Challenges Posed by Regulatory Requirements
If we were to highlight the key requirements arising from the regulations, with a focus on NIS2, these would include requirements related to risk management, supply chain, incidents, and business continuity.
We have compared the maturity levels of these processes among the organizations we work with, across various industries:
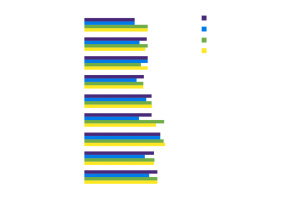
Figure 3. Average maturity level of observed key areas by industry, [Source: Diverto]
- RISK MANAGEMENT
NIS2 defines areas of information/cybersecurity that must at a minimum be covered by a risk assessment and to which technical, operational, and organizational measures must be applied. The aim of applying the measures is to ensure prevention or reduce the impact of the incident to a minimum.
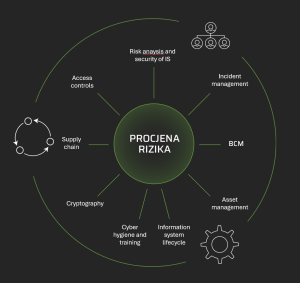
Figure 4. Areas that must be covered by the risk assessment, [Source: Diverto]
- INCIDENT MANAGEMENT
Establishment of a process that includes monitoring, recording and reporting of incidents. Key and important entities must have processes in place to quickly report security incidents with a significant impact on their service delivery or recipients. NIS2 sets specific notification deadlines, such as a 24-hour “early warning”.
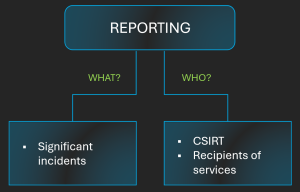
Figure 5. Incident reporting process [Source: Diverto]
- SUPPLY CHAIN MANAGEMRNT
The greatest concerns regarding achieving compliance are related to supply chain management. Specifically, the process of managing the supply chain as required by regulations involves identifying the entire chain of responsibility and acountability. A verified and secure partnership between managed service providers, software and hardware suppliers, and other legal obligors is more important than ever.
In addition to the already known requirements related to supply chain management, it will also be necessary to consider:
- specific vulnerabilities,
- overall product quality,
- the level of information and cybersecurity of suppliers to the end of the supply chain,
- secure product/service development procedures.
- RESILIENCE AND BUSINESS CONTINUITY MANAGEMENT
Along with the basic hygiene of information/cybersecurity, which relates to the level of good habits that users of information and cyber systems have adopted, adhere to daily, and which ultimately help mitigate the consequences of potential incidents, it is inevitable to mention business continuity management. For an organization to ensure resilience and business continuity in the event of unwanted events, it is important to establish a process for managing unplanned situations before and after an incident occurs.
Looking at organizations that are aware and certain they will be subjects to the NIS2/CRA/DORA regulatory frameworks:
- 67% do not discuss information/cybersecurity issues at management meetings or discuss them only in the event of an incident or another (potential) problem related to information/cybersecurity.
- 83% believe that they will be able to achieve compliance with the requirements of the mentioned regulations in time.
- 43% do not have or do not know if they have an established information/cybersecurity management system (ISMS/CSMS).
- 63% think that the CSA is good and covers key areas of cybersecurity necessary for the functioning of the state.
- 30% do not have defined and rehearsed incident response methods.
Check if you are compliant with the NIS2 Directive.
Not 100% sure if the NIS2 Directive applies to your business? You have already taken certain measures and are wondering how compliant you are with its regulations. To more easily assess your security maturity, download the self-assessment tool and begin your journey to compliance with the NIS2 Directive.